RootMe
Enumeration
Using Nmap , we got there are 2 open ports.

Website
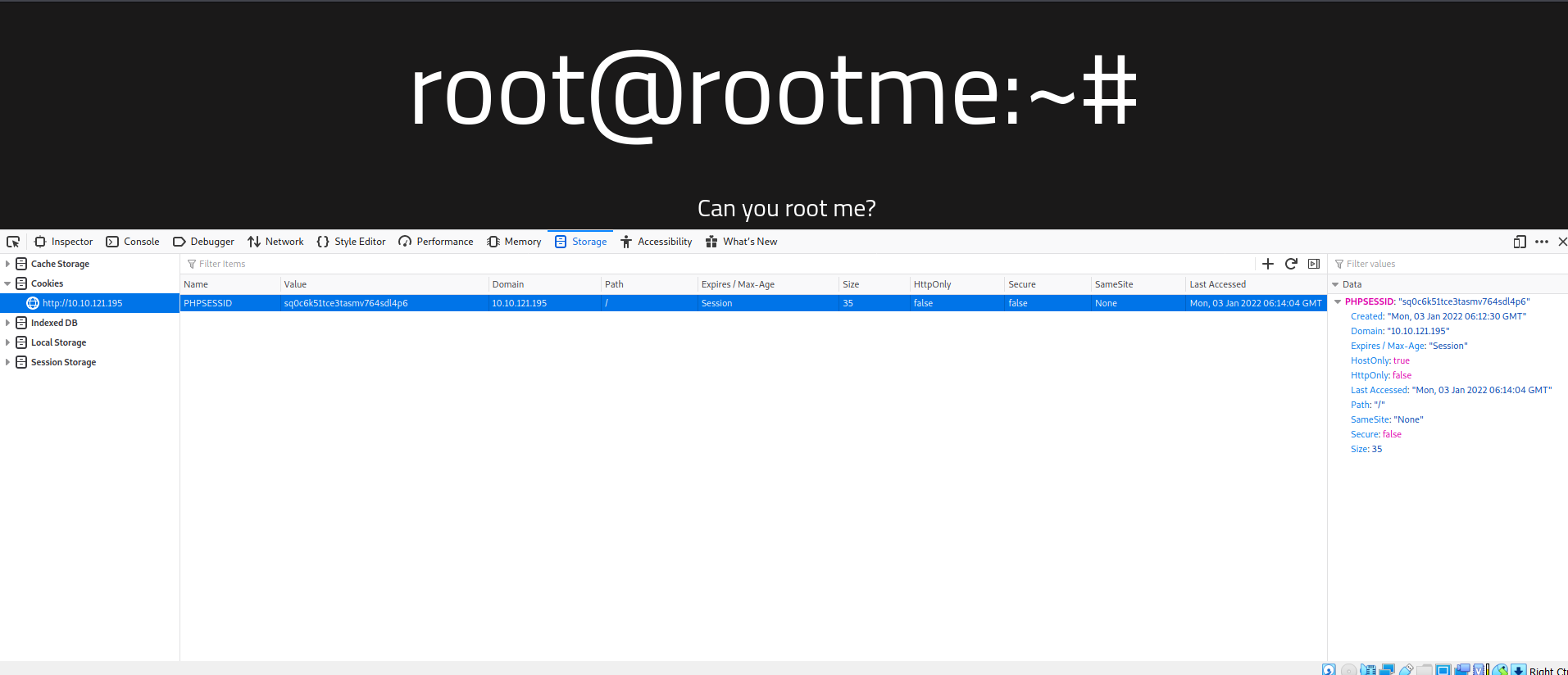
Doesn’t have any hiddent details. Although PHPSESSID is shown indicating PHP is used in backend.
Directory Enumeration
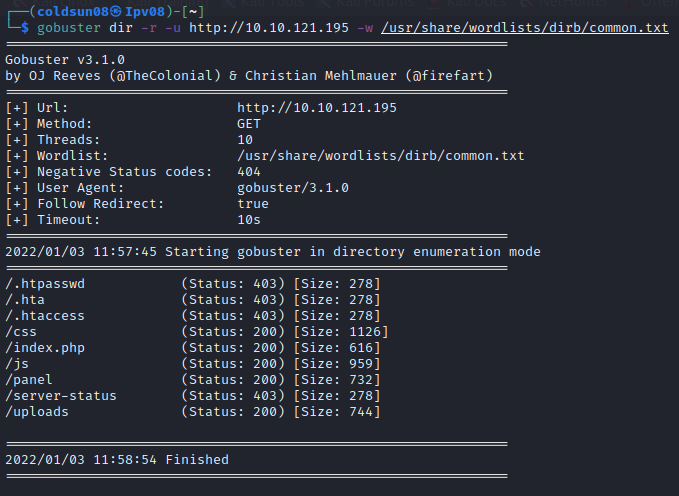
Using gobuster , we get 2 directories like panel and uploads. Panel shows form to upload file. Uploads shows files uploaded from panels form.
PHP Reverse shell
Panel can be used to upload file so I cloned php-reverse-shell repository.

Tried uploading shell but failed.

Googled how to bypass php and found this on website.

Changing .php to .phtml bypassed.

Shell access
Tried running file from opening it through uploads directory. It gave error.

But surprisingly , I got reverse shell.

User flag
Found User flag.

SUID explotation
Tryhackme question specifically asked about SUID so checked for that.

Checked gtfobins python suid.

I got root access.

Root flag
